In this fast-pacing world of technology and computers, you can establish mobile app security using a variety of approaches such as password sharing, zero-knowledge proof, asymmetric keys, end-to-end encryption, and so on.
Furthermore, there are several widely established recommended standards for developing safe mobile apps.
With the growth of the mobile app industry, global enterprises and organizations are embracing modern technology to increase customer communications and employee efficiency. Even companies that have never utilized apps previously are now experimenting with them. Mobile apps are quickly becoming a must-have tool for any company. Most importantly, mobile apps have become an essential part of everyone’s lives, with some even being used to transmit critical data.
However, one key point that many businesses and customers continue to ignore their mobile app security.
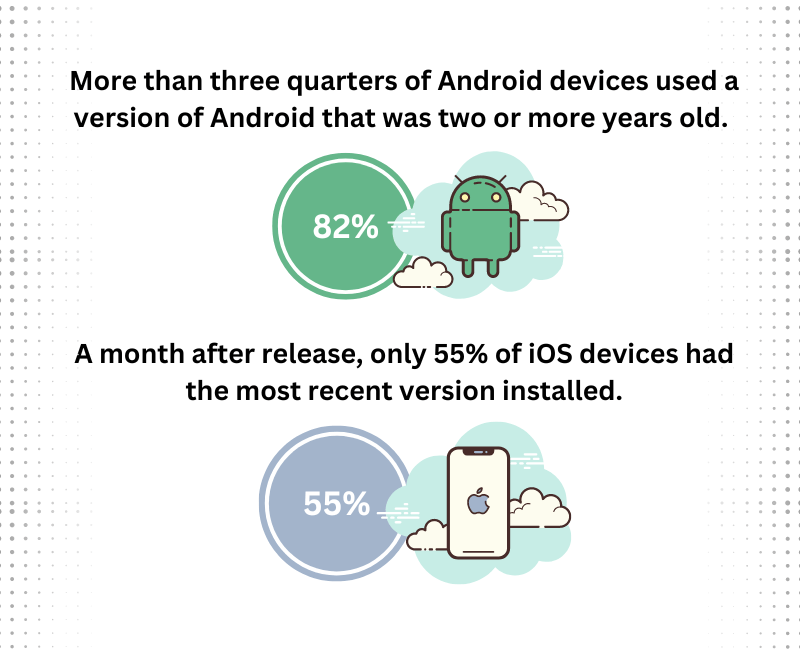
Mobile apps continue to be the primary target for harmful hackers. As a result, enterprises should protect their apps while reaping the benefits that these apps offer. We present a mobile app security checklist that you can use while developing your mobile apps.
WHAT IS MOBILE APP SECURITY?
Mobile app security is a method of protecting applications from external dangers such as malware or any activity that jeopardizes important personal and financial information. Unauthorized users can gain access to not only personal or sensitive information, but also data such as their current location, banking information, and much more.
You may recall that most mobile apps require a user to agree to terms and conditions before starting; it’s safe to say that most consumers skip over the pages of fine language and simply push the “accept” button, assuming that the app manufacturer looks for their best interests at heart.
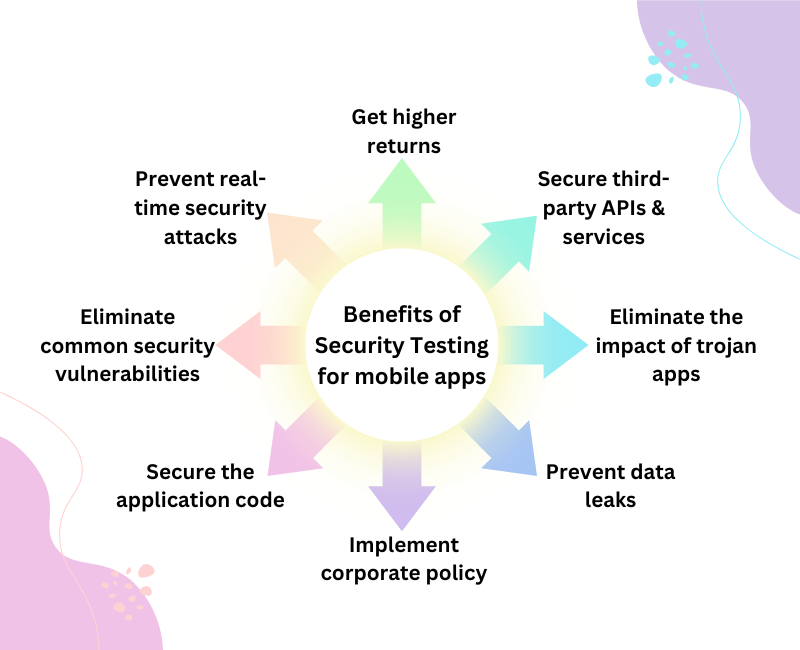
When customers make online purchases or bank transactions, they create a digital trail that includes app information such as their:
- personal name,
- street address,
- phone number,
- Banking app information, etc.
This extremely sensitive app information improves the user experience. However, sensitive data renders us vulnerable to external threats such as hackers if it is stored insecurely. So, when we talk about mobile application security, we mean the precautions we take to protect the applications from external threats that prevent hackers from accessing personal, financial, and confidential data remotely or from lost or stolen devices.
We rarely explore how to safeguard mobile apps until a compromise has already occurred. When this happens, it may be too late to save all of the sensitive app information, therefore it’s best to plan ahead of time for mobile app security.
That’s what we’re discussing today!
HOW TO MAKE ANDROID APPS SECURE?
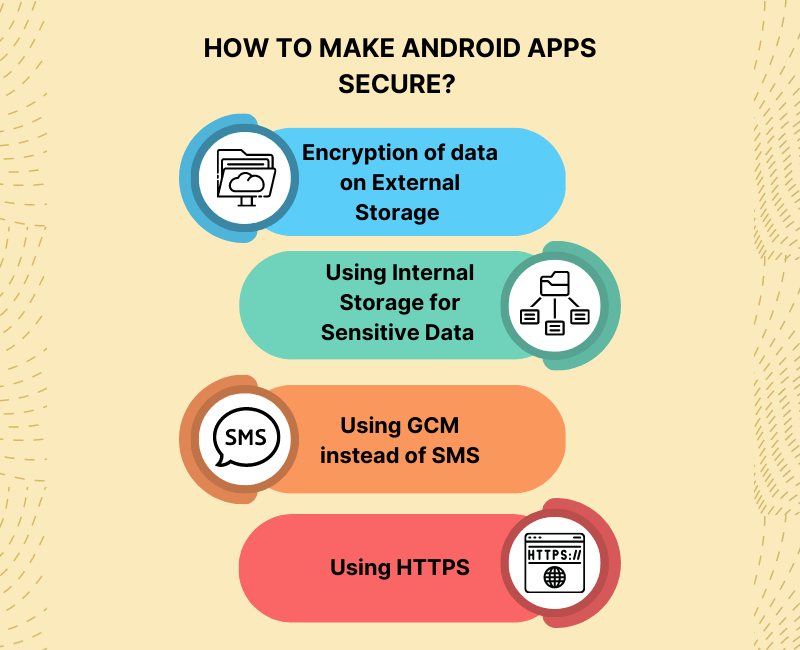
Some effective Android app security best practices to consider are:
Encryption of data on External Storage –
In general, a device’s internal storage capacity is limited. This disadvantage often forces users to rely on external devices such as hard discs and flash drives for data storage. And this data can include sensitive and confidential app information. Because the data on the external storage device is easily accessible by all of the device’s apps, it is critical to save the data in an encrypted format. AES, or Advanced Encryption Standard, is a popular encryption algorithm among mobile app developers.
Using Internal Storage for Sensitive Data –
Every Android application has its own internal storage directory. And the files in this directory are incredibly safe because they are created in MODE PRIVATE mode. Simply said, this mode prevents other apps from accessing the files of a single app saved on the device. As a result, it is one of the best practises for mobile app authentication to concentrate on.
Using HTTPS –
Communications between the app and the server should take place through an HTTPS connection. Many Android users are often connected to multiple open Wi-Fi networks in public places and using HTTP instead of HTTPS leaves the device vulnerable to many rogue hotspots, which can easily change the contents of HTTP traffic and cause the device’s apps to behave unexpectedly.
Using GCM instead of SMS (Short Messaging Services) –
SMS was used to push data from servers to apps when Google Cloud Messaging (GCM) did not exist, but GCM is now widely used. However, if you have not yet switched from SMS to GCM, you should. This is due to the fact that the SMS protocol is not secure nor encrypted. SMS can also be accessed and read by any other app on the user’s device. GCM communications are authenticated on the client side by registration tokens that are reset on a regular basis, and on the server side by a unique API (Application Programming Interface) key.
Other important mobile app development security best practises include user input validation, avoiding the need for personal data before publishing the programme. The goal is to keep app users safe from as much malware as possible.
App security best practices suggested by Google.
HOW TO MAKE IOS APPS SECURE?
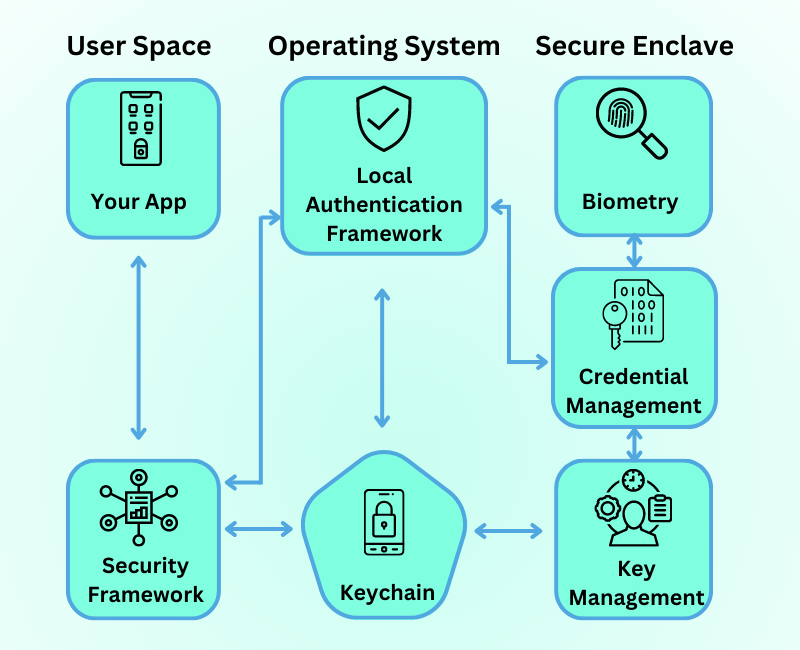
The following are some best practises for iOS app security to follow:
Storage of Data –
The easiest method to drastically simplify your app’s design and increase mobile app security is to save app data in memory rather than writing it to disc or transmitting it to a distant server. However, if saving the data locally is your only choice, there are other options: –
Keychain:
Keychain is the greatest place to keep tiny amounts of sensitive data that don’t require frequent access. Data stored in keychains is controlled by the operating system but is not accessible by any other application. – Caches: If your data does not need to be backed up on iCloud or iTunes, you can keep it in the application sandbox’s Caches directory. – Defaults system: The defaults system is an effortless way to store vast volumes of data.
Networking security:
Apple is well-known for its app security and privacy regulations, and it has worked hard for many years to achieve this level. Apple implemented App Transport Security a few years back, which requires third-party mobile apps to send network requests over a more secure connection, i.e., HTTPS.
Security of Sensitive app Information –
The vast majority of mobile apps make use of sensitive user data such as address book, location, and so on. However, as a developer, you must ensure that all of the app information you request from the user is, in fact, required for access and, more critically, storage. So, if the app information you need can be obtained through a native framework, it is unnecessary to replicate and keep it.
We’ve now seen Android and iOS mobile app security practises for creating a hack-proof app. But no advancement can be as simple as it is described. During every procedure, there will always be some difficulties. Let us learn about the problems that practically every top app development company faces and overcomes.
CHALLENGES ASSOCIATED WITH MOBILE APP SECURITY
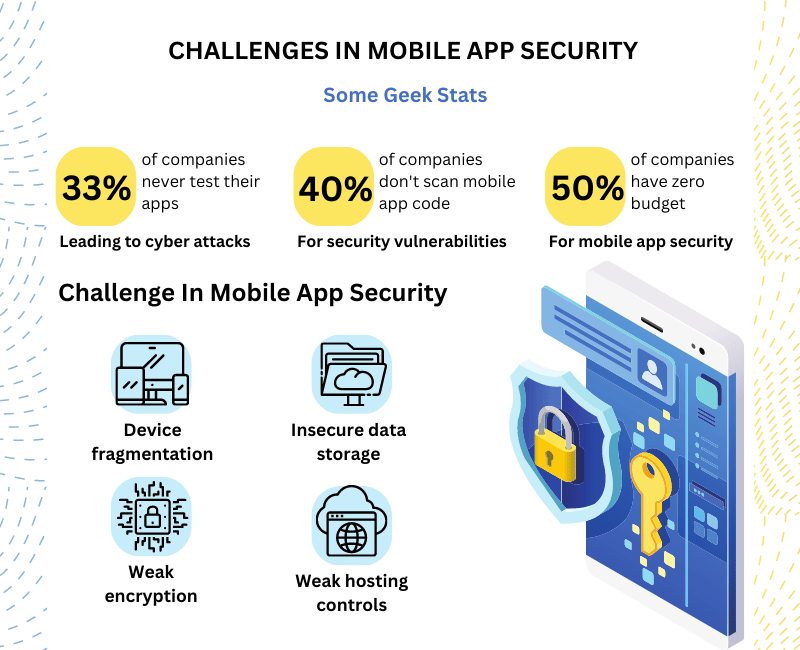
There is a track record of how vulnerable mobile apps can be if adequate mobile app security measures are not implemented to protect them from external threats. The following are some of the issues that may develop if mobile app security testing is not done as needed.
Device Fragmentation –
Before releasing an application to the app stores, some procedures must be followed. It is essential to incorporate a variety of devices with varying resolutions, functions, features, and limits into your mobile app testing procedures. The detection of device-specific vulnerabilities can put app developers one step ahead in terms of app security. Not only are different versions of popular operating systems vital to cover before the app release to cover all possible gaps.
Weak Encryptions –
When encryption is weak, a mobile device is vulnerable to taking data from any available device. Malware attackers are constantly looking for an open end in public mobile devices, and your app could be that open end if you do not follow a rigorous encryption approach. Investing in strong encryption is thus one of the best methods to create a hack-proof mobile app.
Weaker hosting controls –
It often occurs during the construction of a company’s first mobile app, which leaves the data accessible to server-side services. As a result, the servers used to host your app must have adequate app security features in place to prevent unauthorised users from accessing sensitive data.
CHECKLIST FOR MOBILE APPLICATION SECURITY GUIDELINES
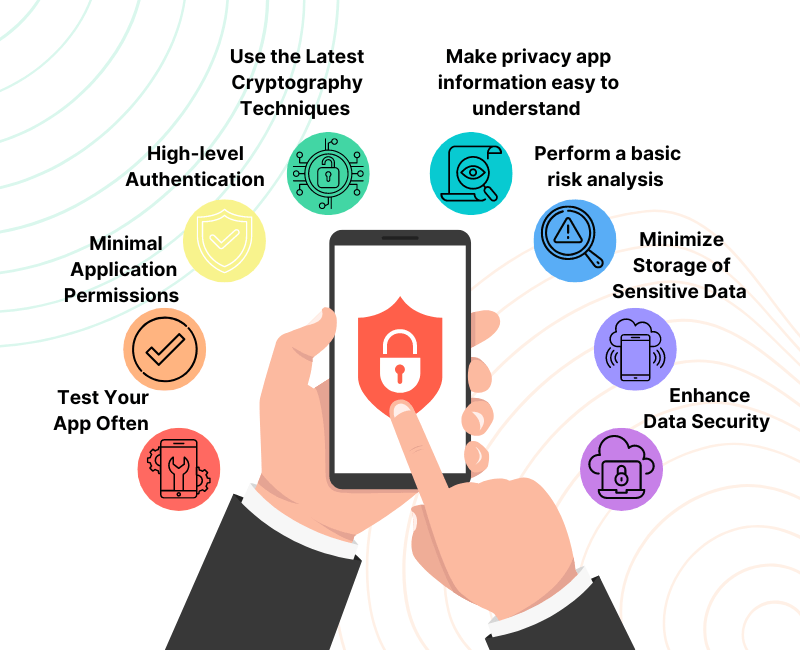
When developing safe applications, every mobile app development business adheres to a number of guidelines. Here is a checklist that app developers often use:
1. Perform a basic risk analysis
Data leaks: Applications with insufficient in-app security are constantly at risk of being penetrated, which can lead to data leaks such as payment credentials, system passwords, and PINs.
Scams: Any app designed to handle financial transactions will always be on the lookout for fraudulent behaviour.
2. High-level Authentication
Security breaches occur due to a lack of high-level authentication. App developers should create apps that only accept strong alphanumeric passwords. Furthermore, it is preferable to make it essential for users to change their passwords on a regular basis. Biometric authentication employing fingerprints or retina scans can be used to increase the mobile application security of particularly sensitive apps. To avoid mobile app security breaches, encourage users to use authentication.
3. Make privacy app information easy to understand
Important app information like this should be provided in a way that the reader can easily understand. For example, rather than a never-ending stream of small print and paragraphs of technical or legal-sounding jargon, make it clear to your user:
- The purpose for collecting data
- The benefit to the user
- What specific personal data is collected
- What the data is used for
- How long data is retained by the app
- How data can be deleted by the user
4. Enhance Data Security
Data security policies and standards should be set to ensure that consumers may easily avoid becoming victims of hackers. This can involve utilising well-implemented data encryption when transferring app information across devices and using firewalls and mobile app security technologies as needed.
5. Use the Latest Cryptography Techniques
Even the most common cryptographic algorithms, such as MD5 and SHA1, often fail to meet the ever-increasing mobile app security demands. As a result, it is critical to stay up to date on the latest mobile application security algorithms and to employ modern encryption methods such as AES with 512-bit encryption, 256-bit encryption, and SHA-256 for hashing wherever possible. Furthermore, you should undertake manual penetration testing and threat modelling on your applications before they go live to ensure failsafe protection.
6. Minimize Storage of Sensitive Data
Developers prefer to put sensitive data in the device’s local memory to safeguard it from users. It is, nonetheless, best practise to avoid storing sensitive data because it may increase the mobile app security risk. If you have no other choice than to store the data, utilise encrypted data containers or a key chain. Additionally, make sure to limit the log by enabling the auto-delete feature, which deletes data after a certain period of time.
7. Test Your App Often
Securing a mobile app is a continuous process. Make regular testing a priority to maintain your app’s security and data safe for users. This continual approach will help you in identifying any potential hazards that may arise.
8. Minimal Application Permissions
Permissions allow applications to operate more freely and effectively. However, they also make apps open to hacker attacks. Mobile apps should avoid requesting permissions outside of their functional area.
There are numerous techniques to create a hack-proof mobile app, including a mobile app security audit, to protect against assaults from unknown sources, and no amount of security measures can ever be sufficient. One approach is to research mobile app development security best practices. Today, the digital world is open to all, and no user is ever immune from viruses and security breaches, but these procedures ensure that your personal data is safe in your digital devices.
We hope this blog helps you in building a safe and secure mobile app!
With Swing2App no code app builder, you get 100% app security, without needing any third-party software or worrying about the above security challenges. Using Swing2App, you can turn your app idea into a reality while enjoying security, technical support, and many more benefits.
